1. Overview
Is an elf32 static and stripped binary, but the good news is that it was compiled with gcc and it will not have shitty runtimes and libs to fingerprint, just the libc ... and libprhrhead
This binary is writed by Ricardo J Rodrigez
When it's executed, it seems that is computing the flag:
But this process never ends .... let's see what strace say:
There is a thread deadlock, maybe the start point can be looking in IDA the xrefs of 0x403a85
Maybe we can think about an encrypted flag that is not decrypting because of the lock.
This can be solved in two ways:
- static: understanding the cryptosystem and programming our own decryptor
- dynamic: fixing the the binary and running it (hard: antidebug, futex, rands ...)
At first sight I thought that dynamic approach were quicker, but it turned more complex than the static approach.
2. Static approach
Crawling the xrefs to the futex, it is possible to locate the main:
With libc/libpthread function fingerprinting or a bit of manual work, we have the symbols, here is the main, where 255 threads are created and joined, when the threads end, the xor key is calculated and it calls the print_flag:
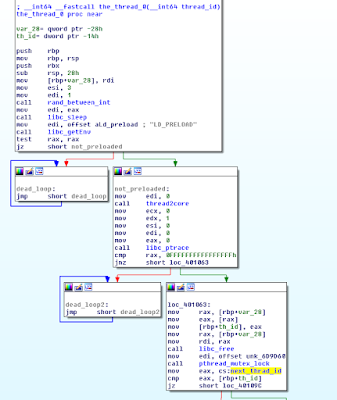
The code of the thread is passed to the libc_pthread_create, IDA recognize this area as data but can be selected as code and function.
This is the thread code decompiled, where we can observe two infinite loops for ptrace detection and preload (although is static) this antidebug/antihook are easy to detect at this point.
we have to observe the important thing, is the key random?? well, with the same seed the random sequence will be the same, then the key is "hidden" in the predictability of the random.
If the threads are not executed on the creation order, the key will be wrong because is xored with the th_id which is the identify of current thread.
The print_key function, do the xor between the key and the flag_cyphertext byte by byte.
And here we have the seed and the first bytes of the cypher-text:
With radare we can convert this to a c variable quickly:
And here is the flag cyphertext:
And with some radare magics, we have the c initialized array:
radare, is full featured :)
With a bit of rand() calibration here is the solution ...
The code:
https://github.com/NocONName/CTF_NcN2k15/blob/master/theAnswer/solution.c
3. The Dynamic Approach
First we have to patch the anti-debugs, on beginning of the thread there is two evident anti-debugs (well anti preload hook and anti ptrace debugging) the infinite loop also makes the anti-debug more evident:
There are also a third anti-debug, a bit more silent, if detects a debugger trough the first available descriptor, and here comes the fucking part, don't crash the execution, the execution continues but the seed is modified a bit, then the decryption key will not be ok.
Ok, the seed is incremented by one, this could be a normal program feature, but this is only triggered if the fileno(open("/","r")) > 3 this is a well known anti-debug, that also can be seen from a traced execution.
Ok, just one byte patch, seed+=1 to seed+=0, (add eax, 1 to add eax, 0)
before:
after:
To patch the two infinite loops, just nop the two bytes of each jmp $-0
Ok, but repairing this binary is harder than building a decryptor, we need to fix more things:
- The sleep(randInt(1,3)) of the beginning of the thread to execute the threads in the correct order
- Modify the pthread_cond_wait to avoid the futex()
- We also need to calibrate de rand() to get the key (just patch the sleep and add other rand() before the pthread_create loop
Adding the extra rand() can be done with a patch because from gdb is not possible to make a call rand() in this binary.
With this modifications, the binary will print the key by itself.
More info
- Hacker Tools Hardware
- Pentest Tools Github
- Hacking Tools For Pc
- Pentest Tools Review
- Top Pentest Tools
- Hacker Tools
- Pentest Tools Url Fuzzer
- Hack Tools For Mac
- Hacking Tools For Mac
- Pentest Tools Framework
- Hacking Tools For Pc
- Pentest Tools Alternative
- Game Hacking
- Hack Tools Github
- Hacker Tools Github
- Pentest Tools Free
- How To Make Hacking Tools
- Hacking Tools Online
- Hacking Tools 2019
- Hack Tool Apk
- Hacking Tools For Windows 7
- Install Pentest Tools Ubuntu
- Nsa Hacker Tools
- Pentest Tools Kali Linux
- Pentest Tools Find Subdomains
- Github Hacking Tools
- Hacking Tools For Windows Free Download
- Hacker Tools Online
- Hacker Tools Free
- Hacking Tools For Windows 7
- Usb Pentest Tools
- New Hack Tools
- Github Hacking Tools
- Hacker Tools Github
- Pentest Reporting Tools
- Nsa Hacker Tools
- Pentest Box Tools Download
- Hacking Tools Github
- Hacking Tools For Windows Free Download
- Hacker Tools Github
- Hacker Tools List
- Hacker Tools Apk Download
- Hack Tools For Ubuntu
- Hack Tools For Mac
- Kik Hack Tools
- Pentest Tools
- Underground Hacker Sites
- Pentest Tools Url Fuzzer
- Hack Tools Online
- Hacking Tools For Windows Free Download
- Hacker Hardware Tools
- Beginner Hacker Tools
- Hack Apps
- Pentest Tools Subdomain
- Computer Hacker
- Termux Hacking Tools 2019
- Hacker Tool Kit
- Hack Tools Pc
- Pentest Tools
- Install Pentest Tools Ubuntu
- New Hacker Tools
- Hacker Tools Apk Download
- Hacker Tools For Mac
- Hacker Tools For Mac
- Hacking Tools For Kali Linux
- Pentest Reporting Tools
- Hacker Tools Linux
- Hack Tools
- Hack Tools Mac
- Hacking Tools For Pc
- Hacker Tools Software
- Hacking Apps
- Tools 4 Hack
- Hack Tools For Windows
- Kik Hack Tools
- Hacking Tools 2020
- How To Hack